5G networks will be more secure but the new technology and the ways we expect it to be used introduce new security challenges and present new questions for regulators to consider.
5G networks will be more secure than previous mobile standards were. Security issues, from the air interface to the core network, have been addressed and mitigated through the standards process in the 3rd Generation Partnership Project (3GPP) and the involvement of bodies like the Internet Engineering Task Force (IETF).
However, security threats are constantly evolving. New technologies and new ways of using them create new vulnerabilities. 5G networks are likely to present new network security challenges due to the advances 5G will bring to mobile technology and the applications we expect it to be used for. To simplify the issues, we identify four core risk areas for 5G networks, and four areas for regulators to consider focusing on.
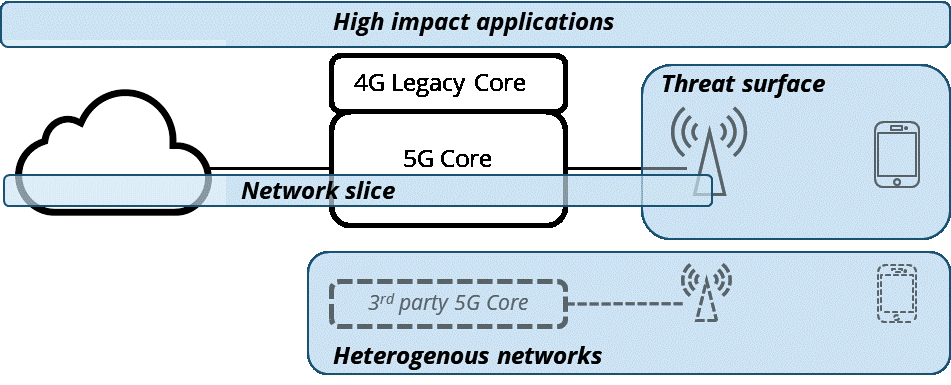
Fig. 1: A simplified 5G network illustrating four core risk areas.
Network Slicing
Network slicing is a popular buzz word and is often accompanied by a complicated diagram with obscure acronyms. Slicing will allow mobile operators to create virtual networks tailored to specific customer requirements and uses. Existing in software, network slices can be quickly created and altered. Slice operators will be able to combine their own software, systems and network elements into a slice.
Potential security threats, such as inter slice security or a compromised slice using all the capacity on shared hardware, have already been identified. As innovative businesses create new and novel ways of using slices, more threats will appear.
Threat Surface
5G will have lots more base stations or cells. There will be many more devices too and the expectation is for lots of 5G connected machines or IoT devices. This means more things that can be attacked and need securing. Careful thought will be needed to secure IoT devices which have often had lower security standards and capabilities. More small cells on street furniture and in buildings mean that physical security will need more careful consideration.
Heterogenous Networks
5G will allow separate networks operated by different entities to work together seamlessly. This does not only include terrestrial networks, but also non terrestrial ones using satellite systems or HAPS. The risks here include whether all the networks have been properly configured and consistent security levels are maintained.
High Impact Applications
Finally, the consequences of future security breaches will also be greater than they currently are. The interruption or damage to important processes transmitted through a compromised 5G network will be expensive and could have lasting effects. Such important processes include information on personal health, medical data or health treatment, autonomous vehicles, smart cities, and manufacturing processes.
Regulation will play an increasingly important role in 5G network security. This is partially due to national security concerns and the strategic need to secure networks that are as important to a country as its electricity supply. As 5G becomes a critical component in new applications, the pressure for regulatory involvement is likely to grow – especially when 5G enters industries that have a historically high level of regulatory oversight like healthcare. Additionally, greater consumer involvement with 5G via new applications and services will require more regulatory involvement.
The questions regulators need to start considering (and 5G network operators too), fall into four categories:
Standards and guidelines – Are existing standards and guidelines such as the ISO27K standards sufficient or should regulators create new ones to meet national and regional requirements?
Innovation – A heavy regulatory hand could stifle innovation in new services, making their creation and launch slow and burdensome. Should regulation be guided by the proportionality of the potential impact of a security breach? Considering technologies such as network slicing are largely software based, are tools such as regulatory sandboxes needed?
Consumers – The burden on consumers for the responsibility of security should be reduced as much as possible. Should regulators mandate a minimum level? What role should regulators and mobile operators play in educating consumers about security principals? Do consumers have a role to play in driving better security behaviours by mobile providers through switching?
Enforcement – In Europe, GDPR fines have drawn attention to data breaches and the security of data. Should a similar approach be applied to 5G networks and does the changing nature of delivery and use mean it could be inappropriate or unfair to place regulatory responsibility for security only on mobile operators?
The value of security is only realised when something goes wrong. Commercially new approaches to insurance and contractual liability may be required as 5G becomes an essential part of our lives. The role of regulators will only grow in importance and that role needs careful consideration before significant security breaches occur.
Author: Chris Adams, Director, Infrastructure, Access Partnership