Many new technologies require high levels of connectivity and new applications are increasingly dependent on the immediate transmission of data. Mobile edge computing (MEC) can help meet this need and improve services to consumers and businesses by shifting the cloud to the edge of the cellular network. However, as with any new technology, MEC brings new regulatory challenges and raises concerns over data, policy and security.
What is Mobile Edge Computing (MEC)?
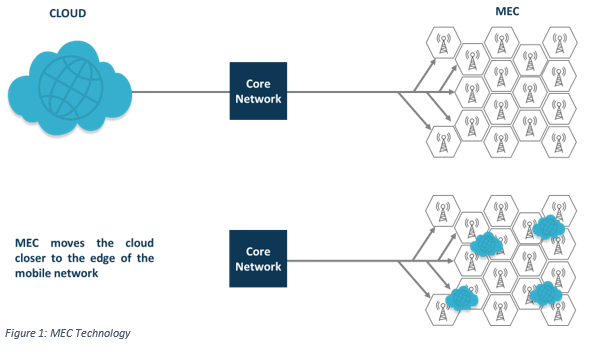
MEC literally does what it says. It places the computing hardware (processing and data storage) at, or very close to, the edge of a mobile (cellular) network, thereby putting the cloud physically close to the base stations or cells that make up the mobile network.
Traditionally cloud services have always been located at the core of the network to maximise economies of scale and efficiency. However, this leads to a relatively long time for a centralised cloud to receive and respond to a request for a service. As the number of connected devices grows, online traffic must travel faster and smarter. MEC will be a solution to the increased demand for cloud storage and processing from the core network. It reduces the latency between base stations and the cloud by bringing data closer to the user and can also access a rich local data set of local network information to improve services to consumers and businesses.
MEC in Practice
Among other applications, MEC can facilitate the widespread adoption of connected cars. Connected cars need to send data between one another, as well as with surrounding infrastructure, with minimal delay (low latency). Upcoming 5G technology allows the creation of virtual networks that run on the physical 5G network infrastructure. Each virtual network can be designed to deliver specific quality of service and tailor performance to specific applications (such as connected cars); this is called network slicing. MEC can be combined with network slicing to guarantee low latency communication, local processing, and support powerful new services and applications that would otherwise not be possible if the cloud functions were located in the core network and information about the local cellular network conditions was not available. With MEC and network slicing, cars in the near future will communicate through their own tailored network.
MEC will also enable video and content delivery with local intelligent caching and optimisation; location services by using real-time accurate local network data, and Internet of Things services and applications that need the benefits of local processing and data storage.
The Mobile Edge Computing Challenge
Before using MEC, industry and public stakeholders must acknowledge the challenges that come with a new technology, including defining a regulatory framework and industry standards that address concerns over security and privacy.
MEC operators, MEC cloud providers, and service and application providers using the MEC cloud already are subject to numerous existing country-specific regulation, such as data localisation and lawful intercept. In most cases, these rules were not developed with edge computing in mind, so developing compliance and regulatory efforts to address them will be particularly challenging. However, new rules will likely develop over time and companies will need to monitor these changes to ensure their compliance across jurisdictions. Finally, policy-makers and industry players will also need to address the privacy, security, and liability implications of giving increased access to new types of data such as real-time user-specific location information.
Author: Chris Adams, Consultant, Access Partnership